From Hours to Seconds: Why Tanium’s Real-Time Visibility is Critical for Modern Enterprises
In modern IT environments, speed and visibility are everything. Organizations manage thousands of endpoints spread across offices, data centers, and remote locations, and traditional tools struggle to keep up. Slow scans, incomplete visibility, and delayed patching aren’t just inconvenient, they’re major security risks.
This is where Tanium stands out.
Often called the Endpoint Management and Security Platform, Tanium delivers something most tools can’t: true real-time visibility and control across every endpoint, even at massive scale.
Tanium is an endpoint management and security platform designed to give IT operations and security teams comprehensive, real-time endpoint visibility, instant data collection measured in seconds rather than hours or days, fast patching and configuration changes, and effective threat detection and response. Tanium also enables unified operations and security workflows. What makes Tanium unique is how it gathers data and issues instructions across endpoints. Instead of relying on heavy servers or expensive infrastructure, Tanium uses a linear peer-to-peer (P2P) communication model that scales extremely efficiently across large and distributed environments.
Tanium uses a modern, distributed architecture built around two core components: Tanium Server and Tanium Clients (installed on endpoints).
Optionally, you can also have Module Servers, Zone Servers (for segmented networks), and if you’re using the SaaS version, Tanium Cloud.
Tanium Server- The Brain of the Platform
The Tanium Server is the central controller. It performs many tasks including authentication and user access, storing results from endpoints, distributing instruction (called “questions”), and managing modules such as Patch, Discover, Comply and Threat Response. The Tanium Server also controls the communication between the console and all endpoints. However, the Tanium Server does not hammer endpoints directly, that’s the secret to scalability.
Tanium Clients- Installed on Each Endpoint
Every managed device, Windows, macOS, and Linux, gets a Tanium Client installed. The client is extremely lightweight, with a tiny footprint and low CPU.
However, it’s not to be underestimated. The client handles many important tasks such as responding to questions, executing actions/patches, forwarding data to the next client in the chain, and maintaining a secure communication channel. While all of this is impressive, the magic is in how the clients communicate with one another.
The Linear Peer-to-Peer (P2P) Chain
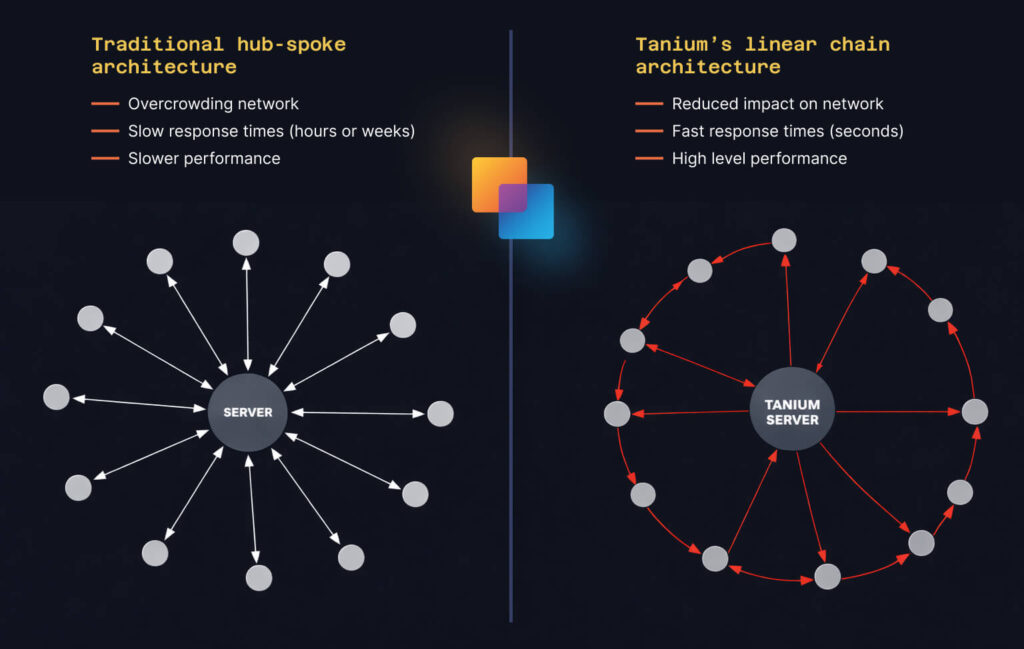
The peer-to-peer chain is Tanium’s patented architecture and is the reason the platform scales to hundreds of thousands of endpoints. The first step in the process is when clients on the same server form a logical chain. The server then sends a question to the first client in the chain. It answers the question, appends its answer, and forwards the question and all collected answers to the next client. The last client in the chain returns the full dataset to the server and awaits its next question.
This peer-to-peer communication is very powerful as it allows near real time results, often under five seconds. Additionally, it allows for minimal server load, doesn’t depend on heavy scanning, and reduces WAN traffic. It is also extremely efficient on large networks, making it ideal for companies of all sizes. The P2P chain is the primary differentiator that traditional tools like SCCM, BigFix, JAMF, etc., do not replicate in the same amount of time. Traditional tools rely on hub-and-spoke models that depend on multiple infrastructure components, resulting in slower data collection and higher operational overhead.
Tanium Modules
Tanium becomes extremely powerful when you activate modules:
- Tanium Discover – Find unmanaged devices
- Tanium Deploy – Software packaging & deployment
- Tanium Patch – OS patching
- Tanium Enforce – Policy + hardening
- Tanium Comply – Vulnerability & compliance scanning
- Tanium Trends – Dashboards & analytics
- Tanium Threat Response – DFIR, EDR capabilities
Modules run on top of the core platform but leverage the same real-time data and P2P communication.
Optional: Zone Servers
Zone servers act as communication proxies for DMZ environments, highly segmented networks, and remote branches with limited connectivity. They relay traffic between clients and the Tanium Server without breaking the P2P chain model.
But why does Tanium’s Architecture matter? Traditional endpoints require bulky and outdated tools such as multiple DPs, MPs, SUPs, (SCCM), scanning engines, network-heavy collections, high server counts, and slow agent wakeups. On the other hand, Tanium’s modern architecture requires only a single Tanium Sever (or a pair for HA), Tanium Clients on endpoints, and optionally one Tanium Module Server.
That’s it.
This simplicity leads to faster detection of vulnerabilities, complete endpoint inventory in seconds, lower infrastructure cost, and overall better reliability across distributed networks.
Contact Us
- Tell us more about your business and what you need from automation and business software.
- One Financial Center
16th Floor
Boston, MA 02111 - Request a Quote: +1 (833) 695-0811